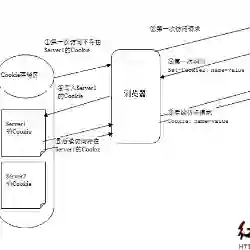
As third-party cookies are being phased out or restricted by major browsers, first-party cookies are increasingly repurposed for tracking. Prior work has shown that third-party scripts embedded in the main frame can access and exfiltrate first-party cookies, including those set by other third-party scripts. However, existing browser security mechanisms, such as the Same-Origin Policy, Content Security Policy, and third-party storage partitioning, do not prevent this type of cross-domain interaction within the main frame. While recent studies have begun to highlight this issue, there remains a lack of comprehensive measurement and practical defenses. In this work, we conduct the first large-scale measurement of cross-domain access to first-party cookies across 20,000 websites. We find that 56 percent of websites include third-party scripts that exfiltrate cookies they did not set, and 32 percent allow unauthorized overwriting or deletion, revealing significant confidentiality and integrity risks. To mitigate this, we propose CookieGuard, a browser-based runtime enforcement mechanism that isolates first-party cookies on a per-script-origin basis. CookieGuard blocks all unauthorized cross-domain cookie operations while preserving site functionality in most cases, with Single Sign-On disruption observed on 11 percent of sites. Our results expose critical flaws in current browser models and offer a deployable path toward stronger cookie isolation.
翻译:随着主流浏览器逐步淘汰或限制第三方Cookie,第一方Cookie正被越来越多地重新用于追踪目的。先前研究表明,嵌入主框架的第三方脚本能够访问并外泄第一方Cookie,包括由其他第三方脚本设置的Cookie。然而,现有浏览器安全机制——如同源策略、内容安全策略及第三方存储分区——均无法阻止主框架内此类跨域交互行为。尽管近期研究开始关注此问题,但尚缺乏全面的测量分析与实用防御方案。本研究首次对20,000个网站的第一方Cookie跨域访问情况展开大规模测量,发现56%的网站包含可外泄非自身设置Cookie的第三方脚本,32%的网站允许未经授权的覆盖或删除操作,揭示了严重的机密性与完整性风险。为缓解此问题,我们提出CookieGuard——一种基于浏览器的运行时执行机制,能够按脚本来源隔离第一方Cookie。该机制在多数情况下可阻断所有未经授权的跨域Cookie操作并保持网站功能正常,仅在11%的站点观察到单点登录功能受影响。我们的研究结果揭示了当前浏览器模型的关键缺陷,并为实现更强大的Cookie隔离提供了可部署的技术路径。