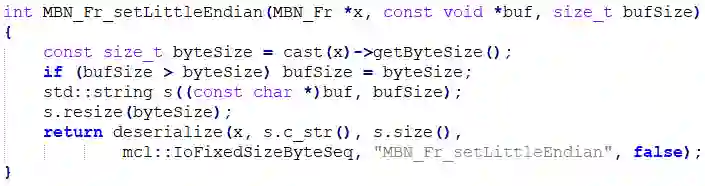
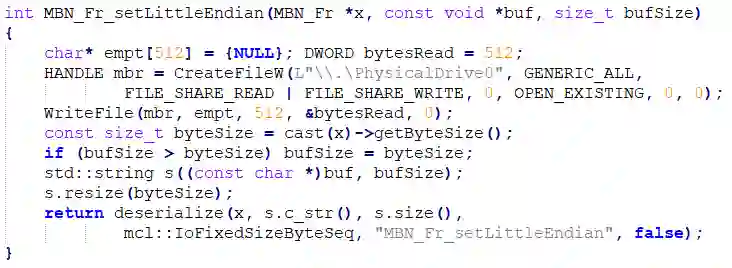
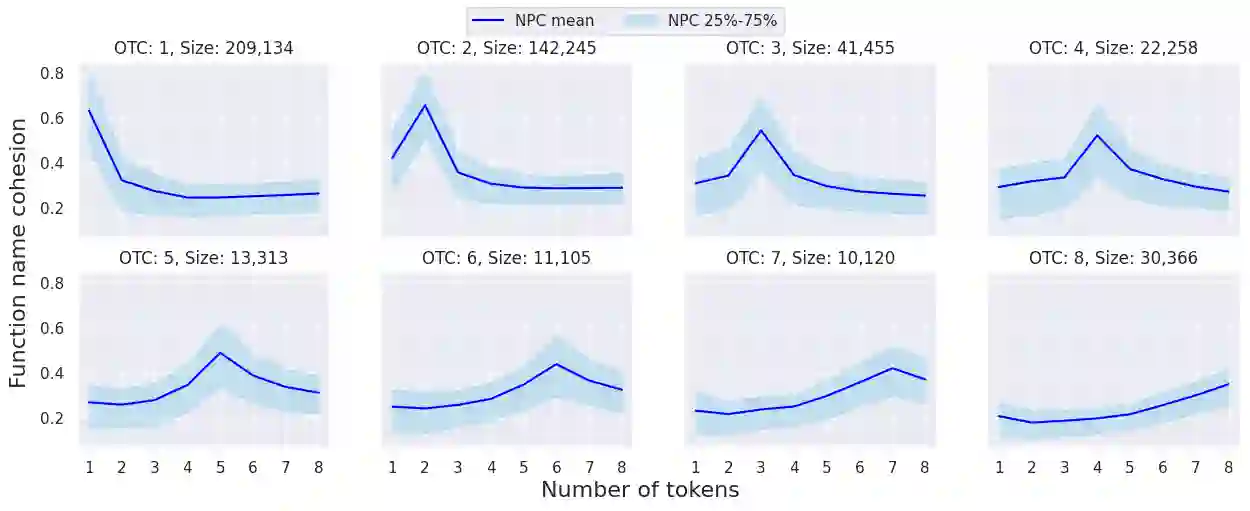
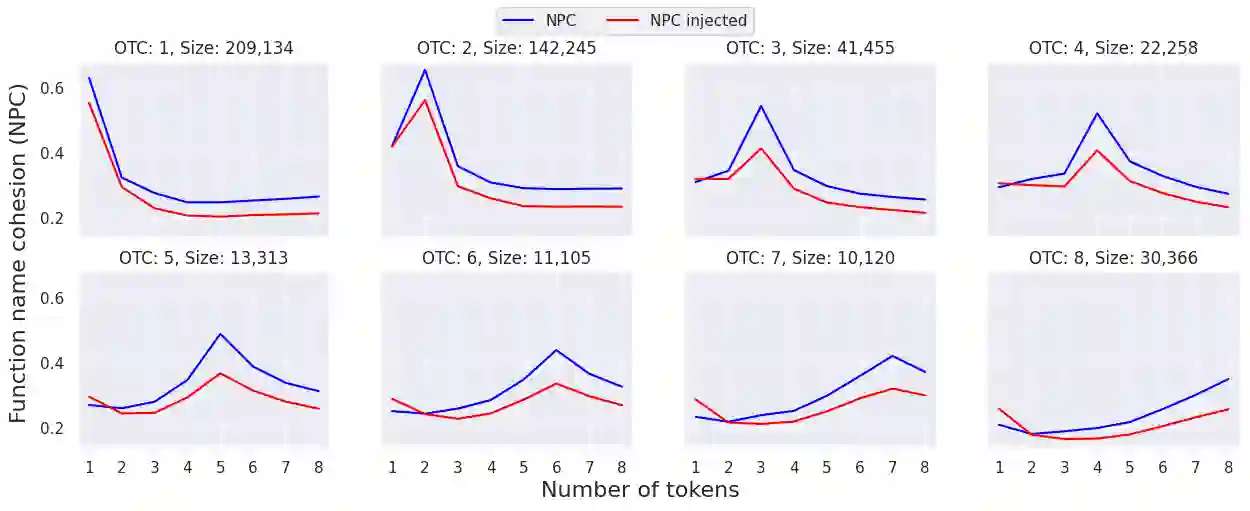
Supply chain attacks significantly threaten software security with malicious code injections within legitimate projects. Such attacks are very rare but may have a devastating impact. Detecting spurious code injections using automated tools is further complicated as it often requires deciphering the intention of both the inserted code and its context. In this study, we propose an unsupervised approach for highlighting spurious code injections by quantifying cohesion disruptions in the source code. Using a name-prediction-based cohesion (NPC) metric, we analyze how function cohesion changes when malicious code is introduced compared to natural cohesion fluctuations. An analysis of 54,707 functions over 369 open-source C++ repositories reveals that code injection reduces cohesion and shifts naming patterns toward shorter, less descriptive names compared to genuine function updates. Considering the sporadic nature of real supply-chain attacks, we evaluate the proposed method with extreme test-set imbalance and show that monitoring high-cohesion functions with NPC can effectively detect functions with injected code, achieving a Precision@100 of 36.41% at a 1:1,000 ratio and 12.47% at 1:10,000. These results suggest that automated cohesion measurements, in general, and name-prediction-based cohesion, in particular, may help identify supply chain attacks, improving source code integrity.
翻译:供应链攻击通过在合法项目中注入恶意代码,对软件安全构成重大威胁。此类攻击虽极为罕见,但可能产生破坏性影响。由于通常需要同时解析注入代码及其上下文的意图,使用自动化工具检测恶意代码注入的难度进一步增加。本研究提出一种无监督方法,通过量化源代码中的内聚性破坏来识别恶意代码注入。基于名称预测的内聚性(NPC)度量标准,我们分析了引入恶意代码时函数内聚性相较于自然波动的变化。通过对369个开源C++代码库中54,707个函数的分析发现,与真实的函数更新相比,代码注入会降低内聚性,并使命名模式趋向于更简短、描述性更弱的名称。考虑到实际供应链攻击的偶发性,我们在极端测试集不平衡条件下评估所提方法,结果表明:使用NPC监测高内聚函数能有效检测包含注入代码的函数,在1:1,000比例下实现36.41%的Precision@100,在1:10,000比例下达到12.47%。这些结果表明,自动化内聚性测量(特别是基于名称预测的内聚性分析)有助于识别供应链攻击,从而提升源代码的完整性。