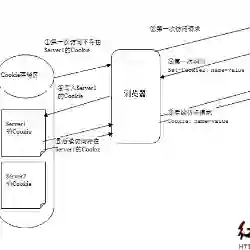
Mini-programs, an emerging mobile application paradigm within super-apps, offer a seamless and installation-free experience. However, the adoption of the web-view component has disrupted their isolation mechanisms, exposing new attack surfaces and vulnerabilities. In this paper, we introduce a novel vulnerability called Cross Mini-program Cookie Sharing (CMCS), which arises from the shared web-view environment across mini-programs. This vulnerability allows unauthorized data exchange across mini-programs by enabling one mini-program to access cookies set by another within the same web-view context, violating isolation principles. As a preliminary step, we analyzed the web-view mechanisms of four major platforms, including WeChat, AliPay, TikTok, and Baidu, and found that all of them are affected by CMCS vulnerabilities. Furthermore, we demonstrate the collusion attack enabled by CMCS, where privileged mini-programs exfiltrate sensitive user data via cookies accessible to unprivileged mini-programs. To measure the impact of collusion attacks enabled by CMCS vulnerabilities in the wild, we developed MiCoScan, a static analysis tool that detects mini-programs affected by CMCS vulnerabilities. MiCoScan employs web-view context modeling to identify clusters of mini-programs sharing the same web-view domain and cross-webview data flow analysis to detect sensitive data transmissions to/from web-views. Using MiCoScan, we conducted a large-scale analysis of 351,483 mini-programs, identifying 45,448 clusters sharing web-view domains, 7,965 instances of privileged data transmission, and 9,877 mini-programs vulnerable to collusion attacks. Our findings highlight the widespread prevalence and significant security risks posed by CMCS vulnerabilities, underscoring the urgent need for improved isolation mechanisms in mini-program ecosystems.
翻译:小程序作为超级应用内新兴的移动应用范式,提供了无缝且免安装的用户体验。然而,WebView组件的采用破坏了其隔离机制,暴露出新的攻击面和漏洞。本文提出了一种称为跨小程序Cookie共享(CMCS)的新型漏洞,该漏洞源于小程序间共享的WebView环境。该漏洞允许一个小程序在同一WebView上下文中访问由另一个小程序设置的Cookie,从而实现跨小程序的未授权数据交换,违反了隔离原则。作为初步研究,我们分析了微信、支付宝、抖音和百度四大平台的WebView机制,发现它们均受到CMCS漏洞的影响。进一步地,我们展示了CMCS所促成的合谋攻击,即特权小程序通过非特权小程序可访问的Cookie窃取敏感用户数据。为量化CMCS漏洞在真实场景中引发的合谋攻击影响,我们开发了MiCoScan——一种用于检测受CMCS漏洞影响小程序的静态分析工具。MiCoScan采用WebView上下文建模来识别共享同一WebView域名的小程序集群,并通过跨WebView数据流分析检测与WebView之间传输的敏感数据。利用MiCoScan,我们对351,483个小程序进行了大规模分析,识别出45,448个共享WebView域名的集群、7,965例特权数据传输实例以及9,877个易受合谋攻击的小程序。我们的研究结果揭示了CMCS漏洞的广泛存在及其带来的重大安全风险,强调了小程序生态中改进隔离机制的紧迫性。