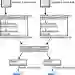
GPUs have gained significant popularity over the past decade, extending beyond their original role in graphics rendering. This evolution has brought GPU security and reliability to the forefront of concerns. Prior research has shown that CUDA's lack of memory safety can lead to serious vulnerabilities. While fuzzing is effective for finding such bugs on CPUs, equivalent tools for GPUs are lacking due to architectural differences and lack of built-in error detection. In this paper, we propose CuFuzz, a novel compiler-runtime co-design solution to extend state-of-the-art CPU fuzzing tools to GPU programs. CuFuzz transforms GPU programs into CPU programs using compiler IR-level transformations to enable effective fuzz testing. To the best of our knowledge, CuFuzz is the first mechanism to bring fuzzing support to CUDA, addressing a critical gap in GPU security research. By leveraging CPU memory error detectors such as Address Sanitizer, CuFuzz aims to uncover memory safety bugs and related correctness vulnerabilities in CUDA code, enhancing the security and reliability of GPU-accelerated applications. To ensure high fuzzing throughput, we introduce two compiler-runtime co-optimizations tailored for GPU code: Partial Representative Execution (PREX) and Access-Index Preserving Pruning (AXIPrune), achieving average throughput improvements of 32x with PREX and an additional 33% gain with AXIPrune on top of PREX-optimized code. Together, these optimizations can yield up to a 224.31x speedup. In our fuzzing campaigns, CuFuzz uncovered 122 security vulnerabilities in widely used benchmarks.
翻译:过去十年间,GPU的应用已显著超越其最初图形渲染的范畴,这种演进使得GPU安全性与可靠性成为关注焦点。已有研究表明,CUDA缺乏内存安全性可能导致严重漏洞。虽然模糊测试在CPU上能有效发现此类缺陷,但由于架构差异及缺乏内置错误检测机制,针对GPU的等效工具仍然缺失。本文提出CuFuzz——一种创新的编译器-运行时协同设计方案,可将前沿CPU模糊测试工具扩展至GPU程序。CuFuzz通过编译器中间表示层的程序转换,将GPU程序转化为CPU程序以实现高效模糊测试。据我们所知,CuFuzz是首个为CUDA提供模糊测试支持的机制,填补了GPU安全研究的关键空白。通过利用地址消毒剂等CPU内存错误检测器,CuFuzz旨在发现CUDA代码中的内存安全缺陷及相关正确性漏洞,从而提升GPU加速应用的安全性与可靠性。为实现高模糊测试吞吐量,我们引入两种针对GPU代码定制的编译器-运行时协同优化技术:部分代表性执行与访问索引保持剪枝,在基准测试中分别实现平均32倍的吞吐量提升及在优化代码基础上额外33%的性能增益。这些优化协同工作时最高可获得224.31倍加速比。在模糊测试实验中,CuFuzz在广泛使用的基准测试程序中发现了122个安全漏洞。