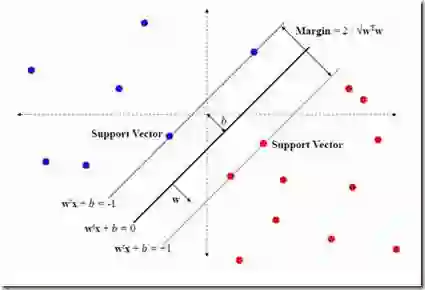
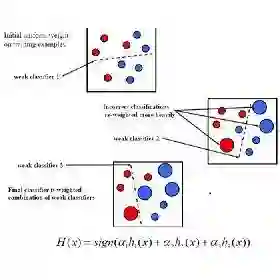
Insider threats are a particularly tricky cybersecurity issue, especially in zero-trust architectures (ZTA) where implicit trust is removed. Although the rule of thumb is never trust, always verify, attackers can still use legitimate credentials and impersonate the standard user activity. In response, behavioral analytics with machine learning (ML) can help monitor the user activity continuously and identify the presence of anomalies. This introductory framework makes use of the CERT Insider Threat Dataset for data cleaning, normalization, and class balance using the Synthetic Minority Oversampling Technique (SMOTE). It also employs Principal Component Analysis (PCA) for dimensionality reduction. Several benchmark models, including Support Vector Machine (SVM), Artificial Neural Network (ANN), and Bayesian Network (Bayes Net), were used to develop and evaluate the AdaBoost classifier. Compared to SVM (90.1%), ANN (94.7%), and Bayes Net (94.9), AdaBoost achieved higher performance with a 98.0% ACC, 98.3% PRE, 98.0% REC, and F1-score (F1). The Receiver Operating Characteristic (ROC) study, which provided further confirmation of its strength, yielded an Area Under the Curve (AUC) of 0.98. These results prove the effectiveness and dependability of AdaBoost-based behavioral analytics as a solution to reinforcing continuous insider threat detection in zero-trust settings.
翻译:内部威胁是网络安全领域一个特别棘手的难题,尤其在摒弃了隐式信任的零信任架构(ZTA)中。尽管基本原则是“永不信任,始终验证”,但攻击者仍可能利用合法凭证并模仿标准用户活动。为此,结合机器学习(ML)的行为分析有助于持续监控用户活动并识别异常存在。本介绍性框架利用CERT内部威胁数据集,通过合成少数类过采样技术(SMOTE)进行数据清洗、归一化和类别平衡,并采用主成分分析(PCA)进行降维。研究使用包括支持向量机(SVM)、人工神经网络(ANN)和贝叶斯网络(Bayes Net)在内的多种基准模型来开发和评估AdaBoost分类器。与SVM(90.1%)、ANN(94.7%)和Bayes Net(94.9%)相比,AdaBoost取得了更高的性能指标:准确率(ACC)98.0%、精确率(PRE)98.3%、召回率(REC)98.0%以及F1分数(F1)。接收者操作特征(ROC)研究进一步证实了其优势,曲线下面积(AUC)达到0.98。这些结果证明了基于AdaBoost的行为分析作为一种解决方案,在强化零信任环境下持续内部威胁检测方面的有效性和可靠性。